SOC 2
Prove SOC 2 with human risk evidence
Evidence Security criteria through awareness and policy records, reduce user-driven incidents, and cut prep time for auditors.

Trusted by organisations to evidence SOC 2 requirements with security training and policy records






























Achieve and evidence SOC 2 compliance
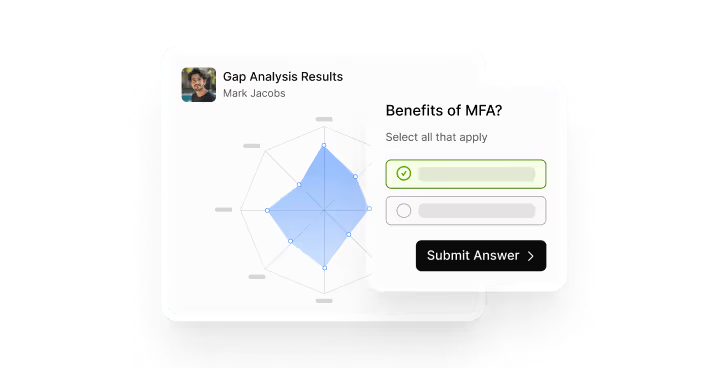
Reduce compliance risk with continuous training
Role-based, automated training modules aligned with CC1.1 and CC2.1 helps you to build employee awareness and document ongoing compliance, reducing risks from human error.
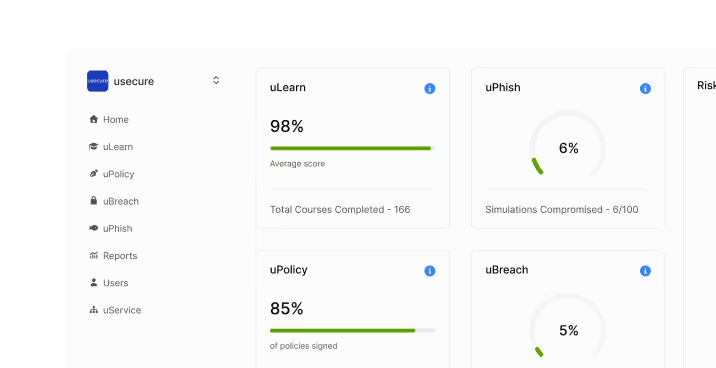
Cut audit effort with centralised evidence
Centralised reporting delivers records of training, policy acknowledgements, and phishing results to support CC4.1 (monitoring activities) and cutting audit prep from days to minutes.
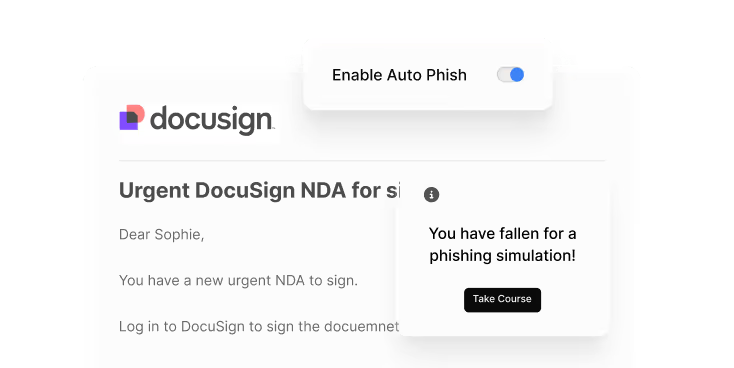
Lower user-driven incidents with behavioural validation
Realistic phishing tests and micro-coaching validate employee resilience against social engineering, aligning with CC7.2 (anomaly monitoring) and CC7.4 (incident response readiness).
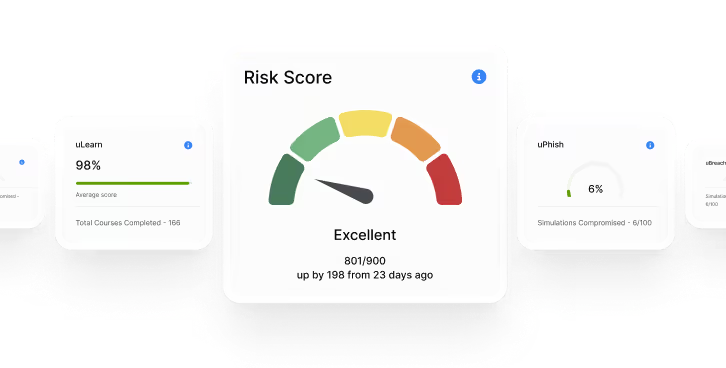
Give auditors and clients confidence efficiently
Dashboards demonstrating human risk level and support Security, Confidentiality, and Privacy principles, providing instant visibility into compliance posture.
Why usecure?
Only usecure unifies training, phishing simulations, policy management, and reporting into a single Human Risk Management platform - trusted by MSPs and IT leaders worldwide to simplify compliance and reduce human risk.
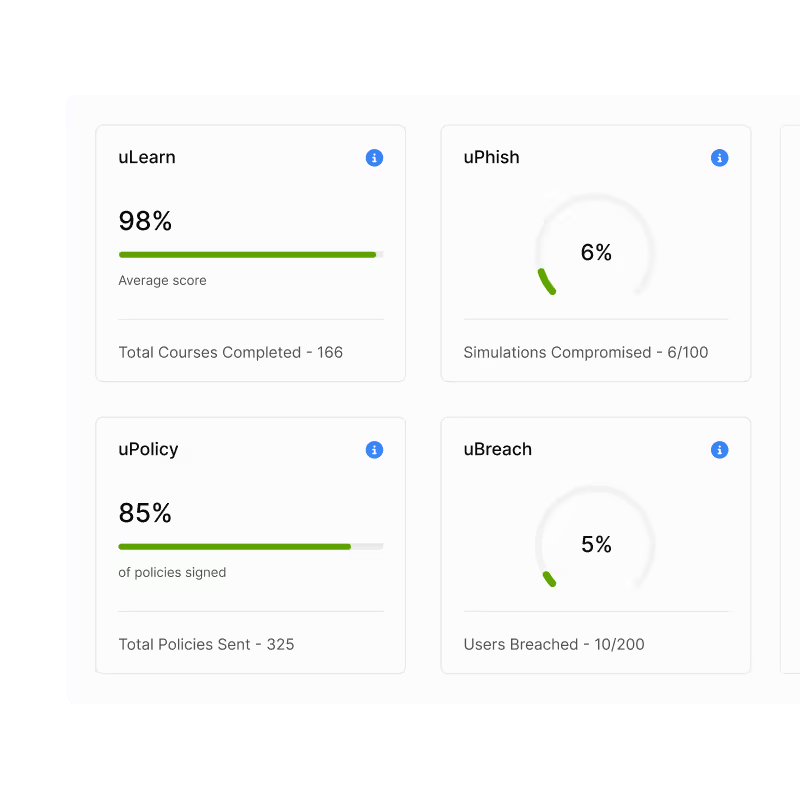
How usecure helps achieve and demonstrate compliance
Whether you’re a single-office law firm or a multi-location consultancy, usecure gives you the automation, visibility, and compliance reporting you need to reduce human cyber risk and protect client trust.
.svg)

.svg)
.svg)






Meets SOC 2 Security criteria
Ongoing security awareness and behaviour validation.
Supports Confidentiality & Privacy criteria
Policies and training on data handling with evidence of acknowledgement.
Policy acknowledgement tracking
Prove policies are communicated and understood.
Behavioural validation
Demonstrate real-world resilience through phishing simulations.
Incident-readiness
Train staff to escalate issues fast in line with SOC 2’s incident response expectations.
Audit-ready reporting
Exportable reports save time and simplify the auditor process.
FAQs
An attestation framework based on the Trust Services Criteria (Security, Availability, Confidentiality, Processing Integrity, Privacy) that evidences effective internal controls.
Every SOC 2 report must demonstrate Security controls, including user awareness, policy enforcement, and incident readiness.
Training, policy acknowledgements, phishing validation, and reporting are captured with timestamps and exportable for auditors.
Yes. Policies, training, and acknowledgements support data-handling and acceptable-use expectations for those criteria.
Yes, manage multiple organisations centrally with per-client automation and reporting.
Still have questions?
Book a meeting with sales for a platform walkthrough and help exploring the features that matter most.


.webp)
.avif)
.avif)